Every brand in every industry delivers on its brand promise through uncompromising focus on what it creates combining what it builds and what it sources from its suppliers. To do that, companies manage their supply chains not just their direct vendors. There is one exception to this rule- our software industry.
Our developers are innovative and smart. They like to do new things. If a capability can be sourced from the vibrant Open Source Software eco-system or bought from a private source, it is appropriate to do that. They then use those components (artifacts) and include them in their software. In-fact, we now assemble our software more than write it ourselves. Industry analysis puts third party code at 70–80 percent of any modern software.

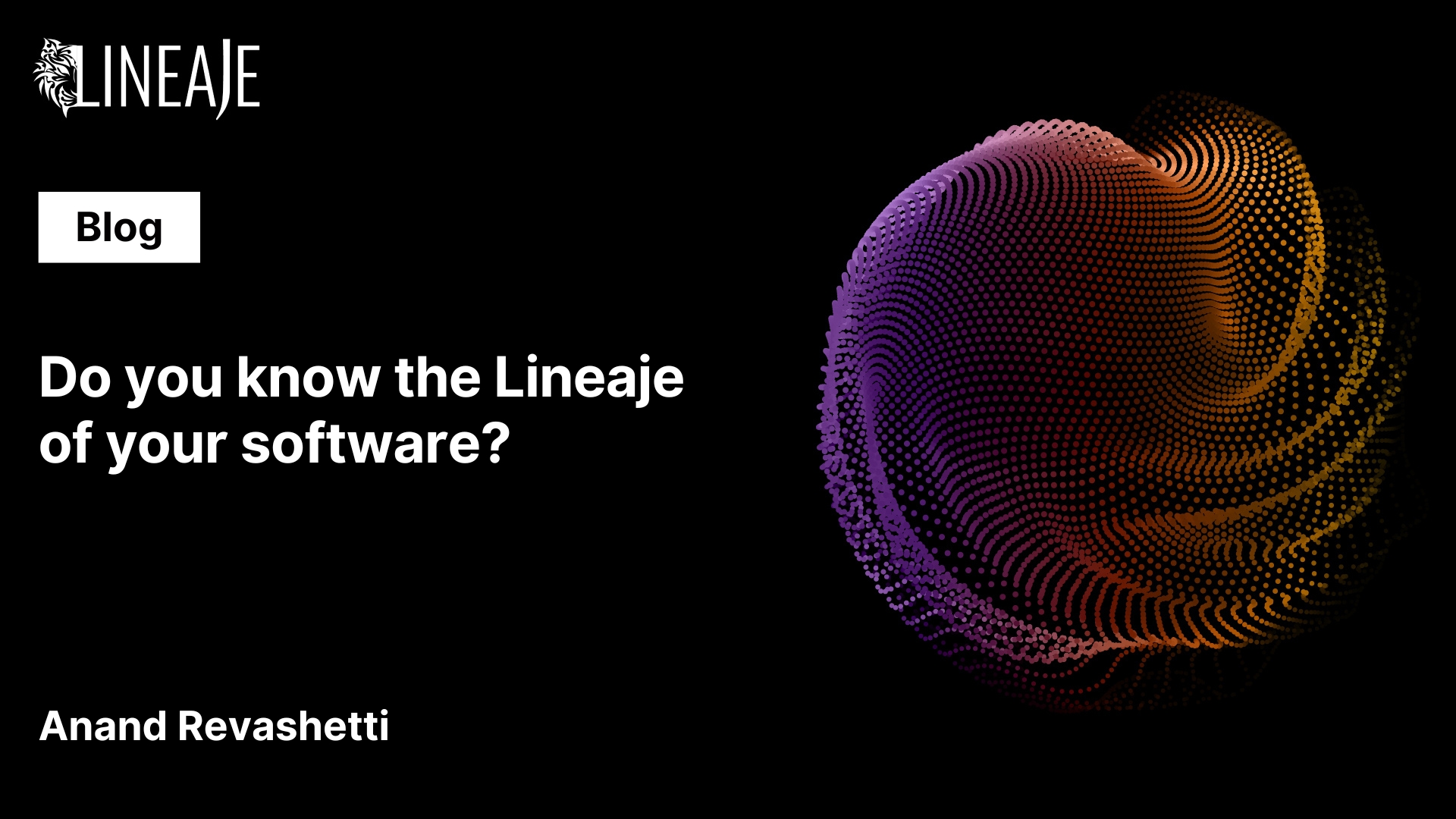
The software we source also has smart developers. Large parts of what they create is also sourced from third parties. And those third-party developers are also smart and so on and so forth. The software we deliver to our customers, contains what are called deep, n-level transitive dependencies embedded inside each artifact.

Some dependencies are static while some are dynamic. And each dependency can continue to change and evolve to the last second it is pulled. So, our software is as still as the ocean. This dynamic nature of software sets Software Supply Chain Management apart from the other, relatively static supply chains other industries deal with.

To compound the challenge, we sometimes source pre-compiled binaries-where we don’t have access to the source code. Our customers don’t know what’s inside those and nor do we. For they too embed third party artifacts from their software supply chain.
And before we deploy the applications we have built, we will pull standard container images which again have deep third party dependencies and are part of our application as we deploy. That adds another layer of opaqueness.
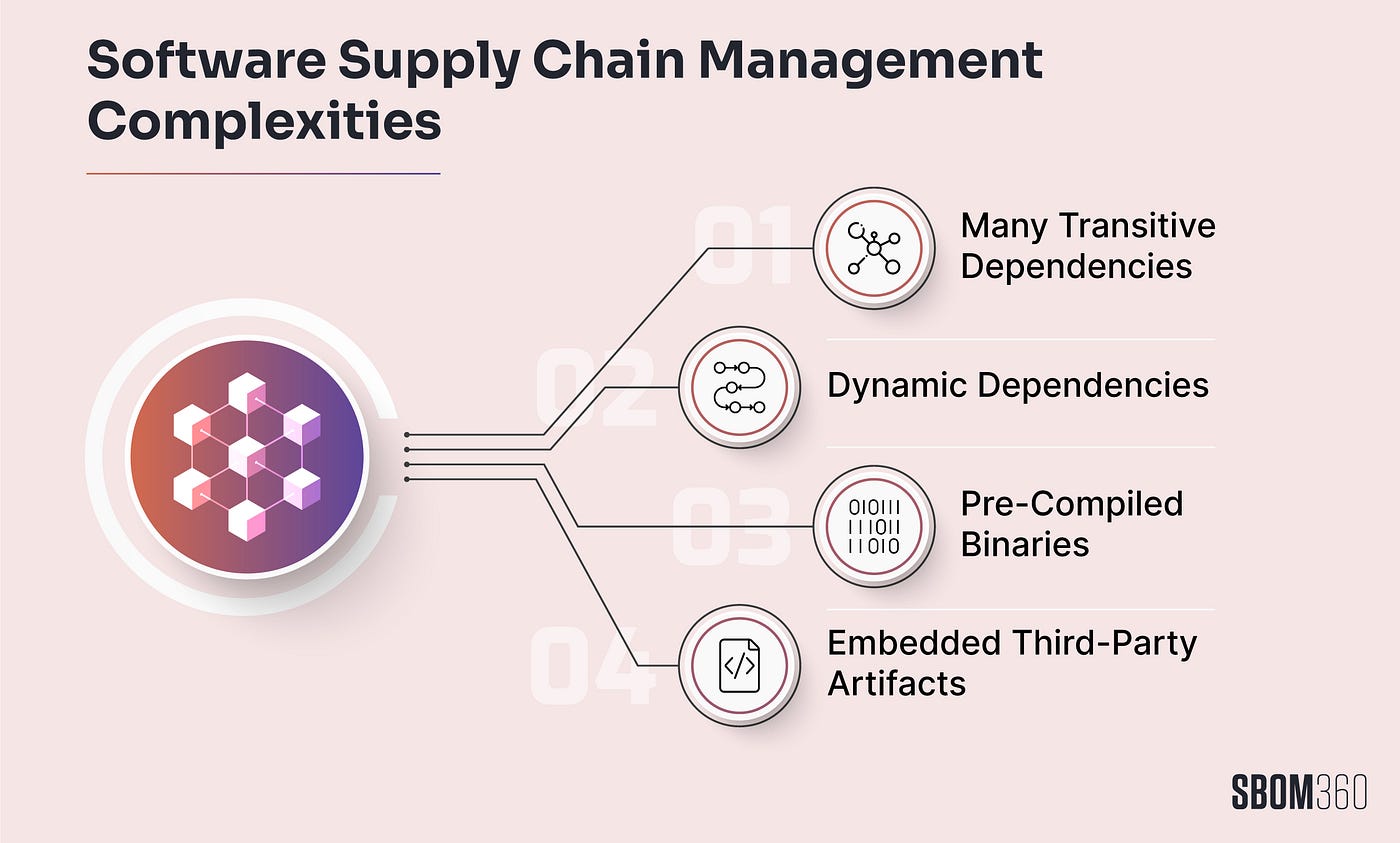
This opaqueness in your software comes from three sources: Open Source Code, Private Code written by your developers and also third party code you sourced from your vendors. Missing any one of these gives you an incomplete picture of your software.
Cybersecurity Executive Order 14028 requires many of us to publish a correct SBOM. The key word there is correct. How important is it to be correct? Think of food labels on food we buy — what is the value of a brand that is incorrectly states its ingredients? Your SBOM accuracy is a direct reflection of your brand.

As supply chain attacks continue to rise, an incorrect SBOM puts your customers at risk. Missing out peanuts as an ingredient in a food label can have a catastrophic impact on peanut-allergic customers as well as on that food brand. Product teams have a special responsibility to ensure the correctness of their SBOM. Your failure to mention your software contains Log4J, and every instance of it, would compromise your customers. The sin of omission becomes a sin that commissions a crime — a breach downstream. Remember Solar Winds.
As software gets deeper into everyday lives of people, we have a special responsibility to build safe, better software. Should your brand be the one that omits to tell your customers that your software contains peanuts? Determining what makes up your software, is too important a call to be left to the whims of individual developers. Remember, the very smart software developers who build our amazing software are experts in their individual domains but software security in not necessarily their gig. This is a collective corporate governance issue. Companies that fail to do this will be exploited — smart hackers will breach them and, unfortunately, their customers.

An omission here, commissions a criminal breach downstream.
And for those companies that use software, insist on an accurate SBOM. If not, you can be SolarWinded by your trusted software vendor.
Our Industry is overwhelmed with vulnerabilities. In fact, we are so overwhelmed with vulnerabilities that we now spend effort & real dollars to prioritize vulnerabilities for us. Smart companies help us find real breach paths and trace execution paths in our software. Why? So we can decide which vulnerabilities are safe for us to not do anything about!

Would you buy a car that had safe vulnerabilities? And people discovered new ones every day. If the car manufacturer could turn around and tell you that they have now found a new critical vulnerability that you should fix for them? Would you buy that car again? The fact is that we discovered 10 High and 32 Medium vulnerabilities every day in 2021.

What’s the Software Supply Chain link here? More than 95% of all vulnerabilities come from our Software Supply Chain. Vulnerabilities are security defects and 95% come from your supply chain. And yet, today, Lineaje analysis shows us that you don’t know who your top software suppliers are and no one in your company has ever evaluated them, spoken to them or probably even heard of them. Why? Software companies don’t manage software supply chain.
Not just who the suppliers are,, we don’t even know if our software has those artifacts that have those vulnerabilities. Today, for most companies, it is a journey of painful discovery to figure out if their software is impacted by a new vulnerability. If you have more vendor software, good luck in finding that out. And if your customers have concerns — your security, product and sales people spend days sorting that out with them An immense loss of productive capacity.
After you have done all that, go back to the opaqueness of the Software Supply Chain we discussed, and you now have an iceberg analogy. Today, you just see the iceberg above water. Under the water line, lies the opaque risk in your software. Get visibility underwater and then manage it. Build a correct SBOM and then manage that SBOM. Your vulnerability pain will drop as you hold your supply chain accountable for what they do to you- everyday.
And this is why we built SBOM360. To solve basic hygiene and integrity issues in the Lineaje of your software.
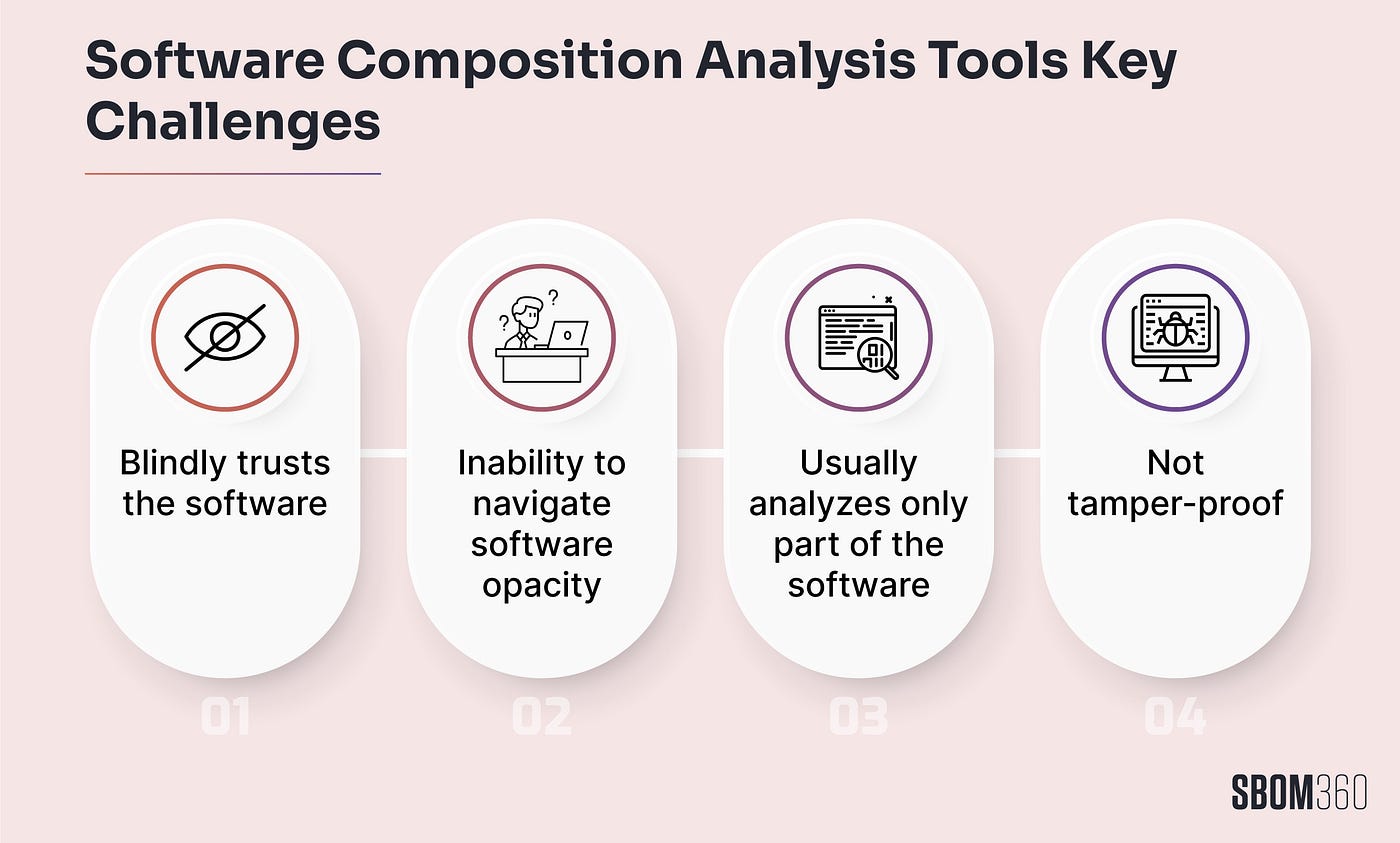
Many Software Composition Analysis (SCA) tools claim that they can create a Software Bill of Materials (SBOM) that discovers what’s in your software. We analysed all SCA tools and found none of them could generate a correct SBOM. Why would that be?

The issues are many but the key challenges are:

Once you have a SBOM, generated by us or by your SCA tool, Shouldn’t you know what your Customers will find when they evaluate it?
Just like we look at ingredients of food labels to decide whether we want to buy a food product, our Customers will evaluate our SBOM. In fact, the US Senate passed a law Supply Chain Security Training act to train federal procurement offices to evaluate software procured for supply chain attacks. Our SBOMs will be exhibit one in that analysis.
A correct SBOM evaluation may bring some bad visibility to you but you also know what you must fix. There is, however, an immediate upside. Once SBOM360 has your SBOM there are hundreds of operational benefits. For example:
SBOM360 is the industry’s first SBOM Manager. Take your SBOM in any standard format and SBOM360 can ingest it in seconds. If you deploy our CLI, we will auto-create your SBOM without the issues of the SCA tools. And then, we will give your our report card on your SBOM. This is what your customers can also find out from your SBOM-especially if they use us to do so.
Never had a SBOM Security policy? Now is the time to create and apply one. If you ship in many countries or have to satisfy many compliance regimes, not a problem — create many policies. SBOM360 evaluates your SBOM against your policies and tell you how your software stacks up.

Because we know more about what your software contains — including OSS and Private Source- we bring-in their transitive dependencies. And you can evaluate your entire SBOM on multiple dimensions including but not limited to Vulnerabilities, Provenance, Licensing, Security Posture, Code Complexity etc.
SBOM360 automatically validates the integrity of your SBOM — the fact that the software artifacts you think you are using is actually the software artifact you are using. And should the reputation of the artifact your developer just used, actually match the security policy you have?
SBOM360 take the long view- you can only improve what you evaluate. We enable you to manage the complete life-cycle of your SBOM from inception to Publish to new versions. To understand how well we do it, explore www.SBOM360.com If we have missed something, work with us. We will make it right for you.
Most software organisations don’t really build just one application. We build hundreds or thousands. If building one correctly and evaluating one is a challenge, how do you do this at scale. Well, once you have done one; SBOM360 has already learnt how to work with you. So SBOM360 will do the rest for you — Shouldn’t that what a SBOM Manger should do? And So it does. Try it.
Comprehensive SBOM Lifecycle Management at your fingertips. Start Small. Evaluate one SBOM. Then Manage All. We will work with you. Explore www.SBOM360.com.
Lineaje is focused on Software Supply Chain Integrity Management. We have much to do. However, as we worked with our initial customers it became abundantly clear that we don’t really know what’s in our software. We can’t manage and secure your Software Supply Chain if you don’t know what’s in your software. So the journey starts with SBOM360.
It’s a small step. It’s the right step. Know your Software Supply Chain first. Start with SBOM360.