

XZ is in the news. The compromise of widely used Linux distros is big news. It is a sophisticated attack. So sophisticated, that the impacted Linux distros shipped it — without catching it! Click here to get a deeper look at what is known about it.
The fundamental issue is — Would the tooling in your CI/CD pipeline have detected this attack? More than 70% of your software is sourced from external suppliers, including your OS — in this case the Linux distribution image published by respective suppliers. However, your CI/CD tools would not detect these types of compromises. Even Microsoft’s sophisticated supply chain tools missed it, leaving it to an eagle eyed developer to raise the alarm.
What technology should you deploy to detect Supply Chain Tampers?
Software integrity attestation is the capability to ensure what you deploy is what you built and what you built comes from your source code. And what you sourced is identical to what was published by maintainers of the source — essentially creating a full chain of attested trust.
XZ attack — from an integrity attestation perspective — boils down to detecting what is shipped (by Linux distros) is validated to be what was published by their open source dependencies. The fingerprints of the installed XZ component in the shipping Linux distros does not match with the one originally published by XZ utility supplier.
In recent years, code signing techniques and “build-system” driven attestations (such as Google’s SLSA approach) have been advocated as valid software integrity attestation solutions. XZ demonstrates that these attestation techniques check the compliance box but fail to achieve the basic goal of attestation — detecting software tampers. In fact- they create a reverse issue- the illusion of untampered software when they certify the attestation of software they know little about.
The supply chain attestation approach matters — Lineaje’s supply chain attestation capability detects the XZ compromise for all our customers. In fact, it detects all such compromises out of the box.
Lineaje Attestation — High Integrity Detection for Identifying Software Supply Chain Tampers:
Lineaje’s attests the integrity of every software component in your supply chain — including all direct and transitive components irrespective of what depth they are in your software supply chain tree. These attestations proactively assess the integrity of software components within the supply chain, to identify tampers and tamper risks.
High-Level Lineaje Attestation Process
Using these parameters, the Lineaje Attestation approach will establish an attestation level for each component in your source code, artifactory, or deployed containers — so if the deployed container contains Linux with XZ utils, it would go through an attestation for its full supply chain.
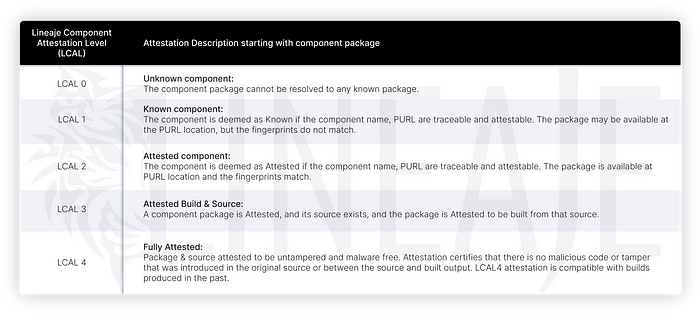
In this compromise, the fingerprints of installed XZ component in the shipping Linux distros do not match the one originally published. Hence even though the component is “known” and the package PURL can be detected, the Lineaje Attestation score will flag it as tampered, or LCAL 1, since the fingerprints of the published component do not match the fingerprints of the installed component.
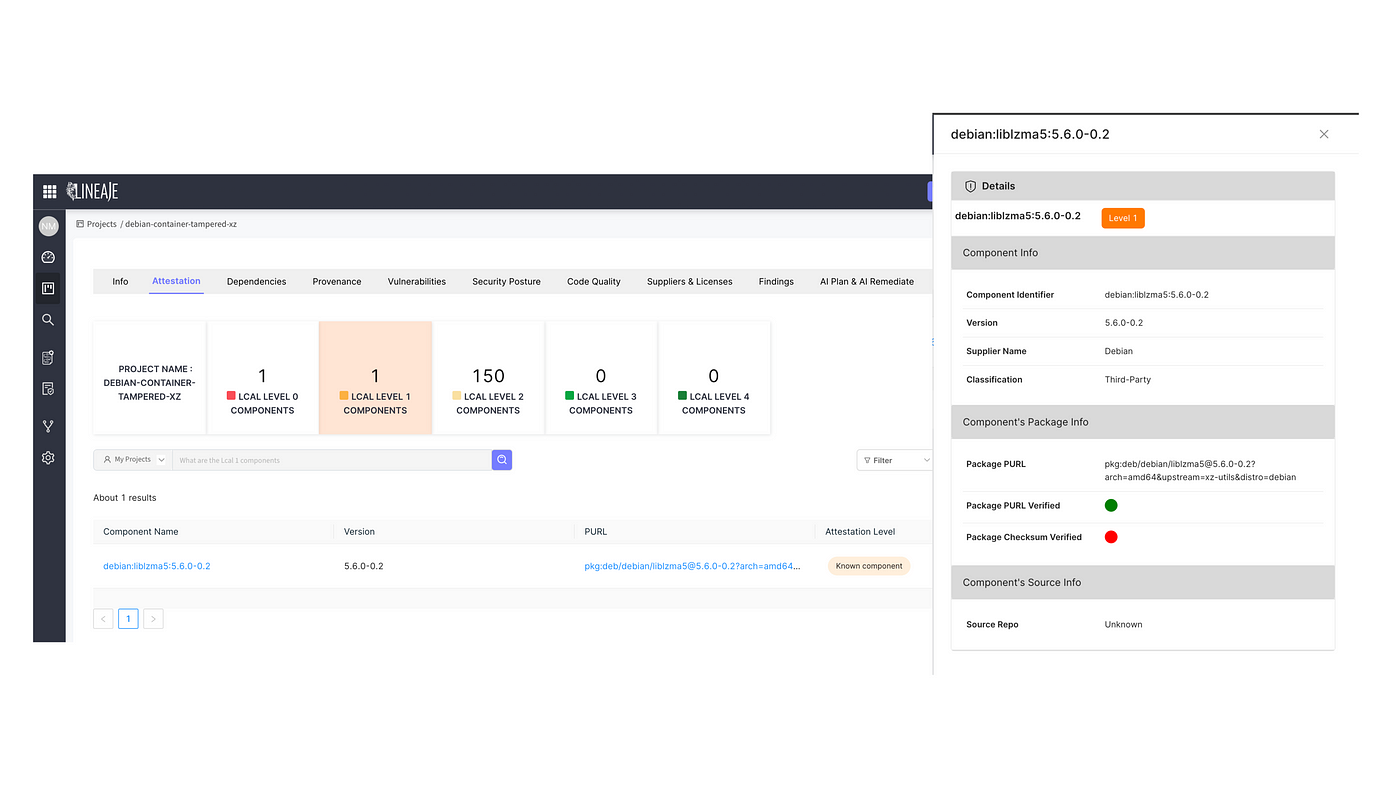
Any component with a Lineaje Attestation score of Level 1 indicates a serious software supply chain tamper and must be addressed immediately.
Conclusion:
As we mentioned earlier, the robustness of the software integrity attestation technology required for the software supply chain is significantly more elaborate than for the CI/CD pipeline. If you want to stay secure, you need Lineaje Attestation.
It’s Time to take back security by managing the integrity of your supply chain not just your CI/CD pipe with Lineaje Attestation — schedule a demo of our capabilities today at www.lineaje.com
#SoftwareSupplyChain #CyberSecurity #ThreatDetection #VulnerabilityManagement #Tamper #BackDoorVulnerability